Waypoint Technology Solutions Blog
The landscape of business is intrinsically tied to technology, and as companies evolve, so does the complexity of their IT requirements. From cybersecurity threats to remote work infrastructure, businesses face constant challenges that demand more than just reactive solutions. To stay competitive and secure while fostering growth, developing a well-thought-out IT strategy is no longer optional—it’s essential.
A well-planned I.T. strategy must think beyond today, it must consider where the business is going, and use the experience of an IT expert to streamline how technology aligns with the business. At a minimum, a strategy should consider the next 5 years.
This blog will walk you through the importance of a comprehensive IT strategy, why it goes beyond individual components, and how aligning technology with business goals is key to long-term success.
What Is an IT Strategy?
An IT strategy is the foundation of how your business uses technology to achieve its objectives. It’s a roadmap designed to align your IT systems, resources, and processes with your company’s goals and values.
But it’s not just about choosing the latest software or hardware. A successful IT strategy takes a holistic view, ensuring that every decision integrates seamlessly across systems, applications, and teams. This alignment ensures resources are used efficiently, risks are minimized, and the business operates at its peak potential.
Why a One-Dimensional Approach Isn’t Enough
Imagine you’re implementing a cybersecurity initiative for your company. The immediate focus might be tightening firewalls or improving encryption protocols, but stopping there is a mistake. Without considering the overall IT environment, you risk creating inefficiencies or leaving gaps that a singular focus can’t address.
For example, have you thought about how your workforce accesses company apps and data? Are they working locally, nationally, or even internationally? Are current systems compatible with the new cybersecurity measures, or will adjustments be needed at the architecture level?
Taking a myopic approach to IT leaves room for costly errors. Instead of looking at isolated projects, businesses need strategies that encompass every layer of their technology system.
The Key Components of a Strong IT Strategy
1. Comprehensive Cybersecurity Framework
Cybersecurity isn’t just about safeguarding data—it’s about ensuring the entire IT ecosystem is secure. A robust strategy evaluates multiple facets, such as how employees log in remotely, data storage protocols, and threat prevention technologies.
Example: You might discover cost-saving opportunities by changing how employees connect to your network. Transitioning from traditional VPNs to Zero Trust network models can reduce recurring expenses while increasing security.
2. System Architecture Alignment
A cohesive IT strategy evaluates how your current systems and architecture interact. Outdated systems may bottleneck productivity or lead to costly inefficiencies. Aligning architecture with business goals ensures that IT supports—not hinders—growth.
Example: Transitioning to cloud-based systems can integrate better with remote work initiatives and scale as your company expands, future-proofing your infrastructure.
3. Remote Workforce Support
The shift to remote work has added layers of complexity to IT requirements. Previously, allowing employees to work exclusively from local offices simplified security and data access needs. Now, companies need strategies tailored to hybrid or fully remote teams spread across different regions.
Considerations include:
- Ensuring uninterrupted and secure access to company applications.
- Adjusting to time zone differences for global teams.
- Managing compliance with international data laws.
4. Proactive Cost Management
Many businesses handle IT reactively, addressing issues only when they arise. This approach often leads to higher costs over time. Instead, a proactive IT strategy evaluates opportunities to reduce expenses without sacrificing functionality or security.
For example, rather than repeatedly investing in new security solutions, reevaluating how users access systems might deliver similar results at a lower cost. Virtual solutions like desktop-as-a-service (DaaS) could provide significant savings compared to traditional setups.
5. Employee Training and Adoption
No IT strategy is complete without ensuring team members are equipped to use the tools you implement. Providing ongoing training not only improves efficiency but also prevents security vulnerabilities caused by human error. A plan that accounts for the human element will always outperform one that doesn’t.
6. Regular Review and Optimization
Technology evolves at lightning speed, making yesterday’s cutting-edge tools obsolete tomorrow. A reliable IT strategy isn’t static—it’s fluid and adaptable, scaling as your company grows and evolves alongside new technological advancements.
Think of it as an iterative process. Reviewing and revising your strategy ensures it remains aligned with both your current needs and the changing tech landscape.
Real-World Impact of a Comprehensive IT Strategy
Businesses that adopt holistic IT strategies gain a competitive edge in several ways:
- Enhanced Productivity - Synchronized systems reduce workflow disruptions, and employees spend less time working around technological inefficiencies.
- Reduced Downtime Risks - Keeping architecture and security updated minimizes risks of data breaches and unplanned system outages.
- Cost Savings - Proactively managing IT eliminates the need for emergency spending and optimizes resource use.
- Stronger Competitive Positioning - Staying technologically agile improves both customer satisfaction and operational scalability.
For instance, several organizations that partnered with IT consultants to create customized strategies reported 30% faster project completions and up to 50% lower cybersecurity costs over just one year. These results emphasize the tangible value of IT planning.
Partnering for IT Success
Developing a comprehensive IT strategy can feel overwhelming. That’s where a reliable IT partner comes in. At Waypoint, we don’t see ourselves as just a service provider. We’re an extension of your team, offering insight, expertise, and proactive solutions tailored to your unique challenges.
Here’s how we help businesses like yours succeed:
- Diagnostic assessments of current IT systems to identify inefficiencies or risks.
- Customized roadmaps for integrating or overhauling technology infrastructures.
- Ongoing support for employees during transitions to new tools or processes.
- Aligning IT with long-term goals to ensure sustainable growth.
Take the Next Step
Technology is no longer just a support tool—it’s the backbone of business operations. Without a thoughtful IT strategy, businesses risk falling behind competitors, overspending, and increasing operational vulnerabilities.
At Waypoint, we believe every organization deserves an ally to help them navigate the complexities of IT, enabling them to thrive in today’s digital world. Whether you’re just beginning to form your IT strategy or need help optimizing your current systems, we’re here to guide you.
Book a consultation with our Waypoint team today and discover how we can help align your IT systems with your business goals.
How seriously does your business take data privacy? Can you back up your answer with concrete examples of what you do to prioritize that notion? Today, we face a serious threat to both individual and consumer data privacy, so we want to take the time to cover how you can make data privacy a priority in your own life.
X The Everything App®, formerly Twitter, has been experiencing a massive user loss for the past few weeks, with everyone from celebrities to average people evacuating from the platform. If you wish to join them for any reason, we’re sharing the process for fully extricating yourself and your data from this specific social media network.
In recent years, there has been much debate about how companies collect, sell, and use personal data. Many businesses make extra money by selling data they collect about people. This might seem like a side effect of all the data we create online, but it can lead to some tricky problems. Today, we'll look at something called the "data-broker loophole," how it works, and what we can do about it.
Cybersecurity is intensely important, so a business owner would think implementing every security feature and defense would be a good idea. However, as research has shown, this can be counterproductive, as only 67% of surveyed security leaders know what led to cybersecurity incidents in their businesses over the past year.
The Disney brand has long cultivated an image of magic and wonder. However, this image has yet to materialize any magical effects in reality. For example, people still suffer from food allergies while visiting Disney’s various parks.
This makes it especially dangerous that a former Disney employee was allegedly still able to access a specialized menu-planning app and make alterations, like changing prices, adding language that Disney certainly would not approve of, switching text to the unintelligible “Wingdings” font, and worst of all… changing menu information.
In June of this year, publisher Chicken Soup for the Soul Entertainment, best known for its book series of the same name, filed for Chapter 7 and Chapter 11 bankruptcy and had many of its assets liquidated. One of these assets was the movie rental service Redbox and its eponymous scarlet rental kiosks, rendering the service defunct.
However, many kiosks remain standing outside businesses even now, which makes us wonder… what about all the data they collected while they were in use?
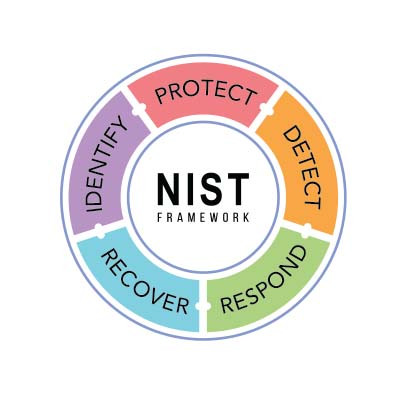
A well-structured framework is essential for establishing effective, consistent policies and strategies. This applies to many areas—including network security. Today, we’re diving into the National Institute of Standards and Technology (NIST) cybersecurity framework, which outlines steps to help safeguard your business.
Let’s have a little fun today. Today’s blog post is written in the format of a daytime soap opera. Please make sure you read all of the dialogue as if being whispered by extremely attractive television stars and starlets!
Life goes on in the small town of Oak Falls, deep woods surrounding the little hamlet nestled on the coast of Cape Seguridad. Let’s follow the lives of some of the residents, their lives Of Vice… and Vulnerability.
There’s never been a more dangerous time to run a business. Okay, maybe that’s not necessarily true, but hear me out. With digital technology taking on a greater importance for businesses than ever before, companies have to contend with countless threats—including the ever-popular phishing scams—regardless of their geographical location.
Modern wisdom states that if you’re not paying for a product, you’re the product.
For all the good the Internet is capable of doing, it is equally capable of being extremely harmful… especially when data is involved. Websites and social media platforms collect data from their users and track their movements across the Internet, sell it to advertisers, and more recently, use it to train AI.
Let’s go over what you can—and arguably should—do to limit these platforms' ability to do so.
It isn’t rare for people to subscribe to things and only stay subscribed because the cancellation process is so challenging and inconvenient. However, the Federal Trade Commission is looking to stop this, adopting a rule that eliminates the capability for businesses to put hurdles in front of cancellation processes.
Let me ask you something: would you trust a bank that locked its doors for the night but left all its cash in a big pile in the middle of the floor? Probably not—after all, if someone managed to get through the doors, nothing would stop them from helping themselves to the funds inside.
This is effectively how cybersecurity once worked, with the presumption that if someone had access to a network, they had permission to access any data on it. Fortunately, many businesses have made the switch to a better approach, known as zero-trust security.
Windows 11 takes a page out of Apple’s design playbook and features a taskbar that, instead of being off to the side, is smack in the middle of the toolbar. While some may like this change, others may not.
Fortunately for these others, a simple setting change can return the taskbar to its familiar place like on older versions of Windows.
You're at a crossroads with your current "IT Guy" or Managed Services Provider (MSP) because you're spending money and continually having problems. Well, you're not alone... When looking for an IT partner, you're looking for competence. Someone who can speak to your industry and your business, help translate the IT talk, and keep your systems running while helping guide you into the future.

How do you decide what type of IT partner you need?
Selecting the right Managed Service Provider (MSP) for your business is a crucial decision that can significantly impact your operations and overall success. A study found that over 90% of MSPs generate less than $1 million in annual gross revenue, which implies that many of these providers consist of just one or two individuals. At the same time, this may seem appealing due to the potential for personalized service or the false perception of a lower cost. A small team often lacks the resources and expertise to consult, guide, and implement comprehensive solutions tailored to your business needs. The single "IT Guy" MSPs do have a purpose; they mainly work on the "break-fix" model, which means you call when something breaks, and they fix it. They work well in boutique businesses, say a Dentist's office or a Retail store, where they don't need to be an expert but just technical enough to keep their clients running. These guys may not fit your needs if you're in a more technical, regulated, and process-driven industry.
When considering larger MSPs—with 15 or more employees—weighing the pros and cons is essential. Larger firms typically possess a broader range of expertise, rigorous processes, and greater scalability, allowing them to handle complex IT environments effectively. However, many larger Managed Services Providers (MSPs) are service teams in a more prominent technology solutions company. These companies can be $50-500 million dollar organizations that work in the enterprise organizations and are owned by venture capital companies. These organizations tend to be more sales-focused and often operate nationally, meaning a team member in a different state could address your issue when you call for support. Depending on the provider's structure, this can lead to delays in service and a lack of personalized support or tribal knowledge of your business. Additionally, they often must restrict service to increase profitability and rarely act in your best interest.
Then there is Waypoint. At Waypoint, we focus on service, value, and customized IT solutions that fit your industry, strategy, and budget. We don't consider ourselves your IT Service Provider but an extension of your team, looking out for your best interests and focused on a long-term relationship built on trust. We have experienced IT experts in many fields and a network of consultants across the globe.
When choosing an IT provider, it's not about how large or small the company is; it's about competence and resourcefulness.